OAuth (Open Authorization) is an open standard protocol used for authorization. It allows third-party applications to access a user’s resources on another service without exposing their credentials, like passwords.
Here’s a breakdown of how OAuth works:
Key Concepts:
- Resource Owner (User): The entity that owns the data or resource.
- Client (Application): The third-party application requesting access to the resource.
- Resource Server (API): The server hosting the protected resources (e.g., APIs).
- Authorization Server: The server that authenticates the resource owner and issues access tokens to the client.
How OAuth Works
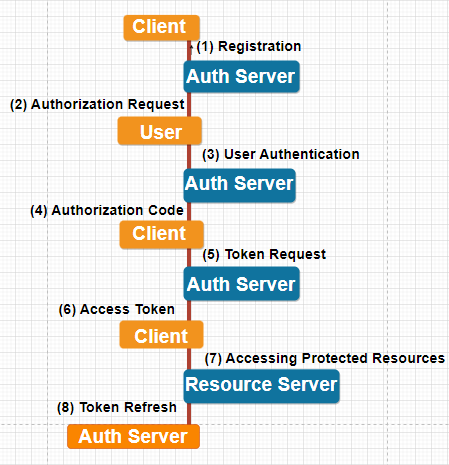
Step 1: Registration
- The client (e.g. a web application) registers with the authorization server (e.g. Google, Facebook) and receives a client ID and client secret.
- The client ID is a public identifier for the client, and the client secret is a confidential key used to authenticate the client.
Step 2: Authorization Request
- The client (e.g. a web application) redirects the user to the authorization server’s authorization endpoint.
- The client includes its client ID, response type (e.g. code), and redirect URI in the request.
- The user is prompted to authenticate with the authorization server.
Step 3: User Authentication
- The user authenticates with the authorization server using their credentials (e.g. username and password).
- The authorization server verifies the user’s credentials and checks if the user has authorized the client to access their resources.
Step 4: Authorization Code
- If the user authenticates successfully, the authorization server redirects the user back to the client with an authorization code.
- The authorization code is a short-lived token that can be exchanged for an access token.
Step 5: Token Request
- The client sends a request to the authorization server’s token endpoint to exchange the authorization code for an access token.
- The client includes its client ID, client secret, and authorization code in the request.
Step 6: Access Token
- The authorization server verifies the client’s credentials and the authorization code, and issues an access token if everything is valid.
- The access token is a long-lived token that can be used to access the user’s resources.
Step 7: Accessing Protected Resources
- The client uses the access token to access the user’s protected resources (e.g. API endpoints).
- The resource server verifies the access token and grants access to the resources if it is valid.
Step 8: Token Refresh
- When the access token expires, the client can use a refresh token to obtain a new access token.
- The refresh token is a long-lived token that can be used to obtain a new access token when the current one expires.
Use Cases:
- Single Sign-On (SSO): Allowing users to log in to multiple services using a single set of credentials.
- Third-Party App Access: Granting third-party applications access to user accounts on platforms like Google, Facebook, or GitHub without sharing passwords.
OAuth Versions:
- OAuth 1.0: The original version, more complex with two tokens.
- OAuth 2.0: The more commonly used version, simplified and more flexible.
Conclusion:
OAuth enables secure access to user data by third-party apps without sharing passwords, using access tokens to define permissions. It’s essential for protecting user privacy while allowing seamless interactions between systems.