API Policies?
Anypoint Platform API policies are a set of rules that can be applied to APIs to ensure their security and compliance with organizational requirements
Policy Categories
Anypoint Platform offers a wide range of API policies, which can be categorized based on the functionality they provide. Some common categories include:
- Security Policies
- Compliance Policies
- Transformation Policies
- Quality of Service (QoS) Policies
- Troubleshooting Policies
- Security Policies:
These policies focus on enforcing authentication mechanisms such as Basic Authentication, OAuth 2.0, or JWT (JSON Web Tokens). They also enable access control based on IP addresses, allowing or denying access to API endpoints based on predefined IP ranges. Ensuring the security of APIs is crucial to protect sensitive data and prevent unauthorized access.
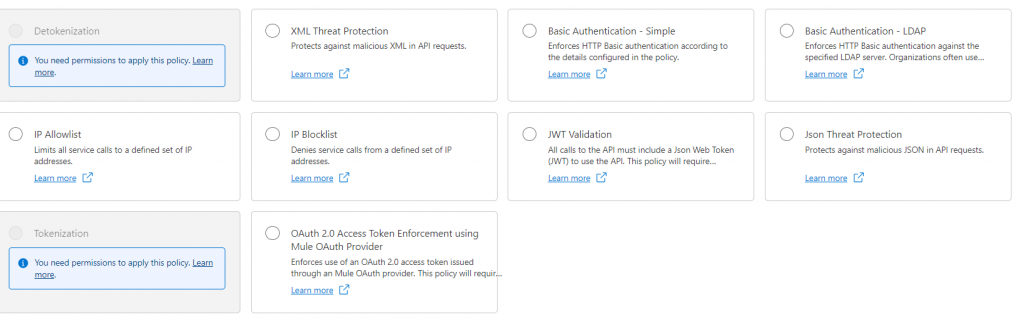
- OAuth 2.0: OAuth (Open Authorization) is a standard protocol for authorization that allows third-party applications to access user data without the need to share user credentials. It enables users to grant access to their resources stored on one site (like a social media platform) to another site or application (like a mobile app) without revealing their passwords. OAuth 2.0 provides a secure and standardized way for applications to access protected resources on behalf of the resource owner.
- JWT Validation: JWT (JSON Web Token) Validation is a security policy that allows you to validate incoming requests using JWT tokens. JWT is a compact, URL-safe means of representing claims to be transferred between two parties. The policy verifies the signature of the token and checks the values of the claims to ensure the integrity and authenticity of the request.
- Tokenization / Detokenization: Tokenization is the process of replacing sensitive data with a unique identifier or token. This helps protect sensitive information such as credit card numbers or personal identification numbers (PINs) by storing the tokens instead of the actual data. Detokenization is the reverse process, where the token is replaced with the original sensitive data. This policy helps in securing sensitive data while allowing authorized access when needed.
- Basic Authentication: Basic Authentication is a simple authentication scheme built into the HTTP protocol. In this method, the client sends HTTP requests with an Authorization header containing the word “Basic” followed by a space and a base64-encoded string of the username and password concatenated with a colon. While easy to implement, Basic Authentication is considered less secure compared to more advanced authentication methods like OAuth 2.0.
- JSON / XML Threat Protection: JSON/XML Threat Protection is a security policy designed to protect APIs from various types of attacks, including those targeting JSON or XML payloads. This policy helps prevent attacks such as JSON/XML injection, where attackers manipulate JSON or XML data to execute malicious code or exploit vulnerabilities in the API server. The policy analyzes incoming requests for signs of malicious activity and blocks or mitigates threats accordingly.
- IP Allowlist / Blacklist: IP Allowlist (also known as Whitelist) and IP Blacklist are security policies used to control access to resources based on the source IP address of incoming requests. With IP Allowlisting, only requests from specified IP addresses or ranges are allowed access to the protected resource. Conversely, with IP Blacklisting, requests from specified IP addresses or ranges are denied access. These policies help enforce access control and protect against unauthorized access attempts.
2. Compliance Policies:
Compliance policies are designed to enforce regulatory or organizational requirements. For example, they may require clients to provide a valid Client ID to access the API or enforce Cross-Origin Resource Sharing (CORS) rules to control access from web applications running in different domains. Compliance policies help ensure that APIs adhere to industry standards and organizational guidelines.
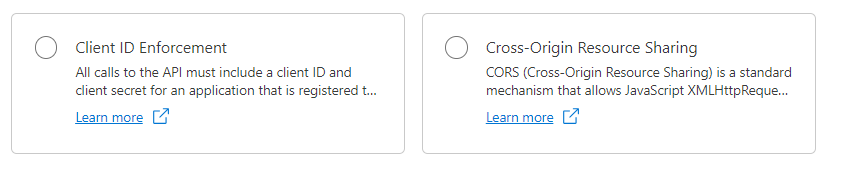
- Client ID Enforcement: The Client ID Enforcement policy is a security measure that restricts access to a protected resource by allowing requests only from registered client applications. Each client application is assigned a unique identifier known as a Client ID, which must be included in the request headers when accessing the API. This policy ensures that only authorized clients, whose credentials have been approved, are allowed to consume the API. By enforcing client ID validation on each request, the policy helps prevent unauthorized access and ensures that only trusted clients can interact with the API.
- CORS (Cross-Origin Resource Sharing): CORS is a mechanism that allows web browsers to make cross-origin requests, i.e., requests for resources from a different domain than the one serving the current web page. It is a security feature implemented by web browsers to prevent malicious websites from making unauthorized requests to other domains. CORS works by adding HTTP headers to responses from the server, indicating whether the requested resource can be accessed by the requesting domain. The CORS policy allows you to configure which origins are allowed to access your API’s resources, thereby controlling cross-origin requests and protecting against potential security vulnerabilities such as cross-site request forgery (CSRF) attacks.
3. Transformation Policies:
These policies allow for the transformation or enrichment of request or response headers. This can involve adding, removing, or modifying header information to meet specific requirements. For example, headers may need to be modified to comply with backend system specifications or to enhance security by removing sensitive information.
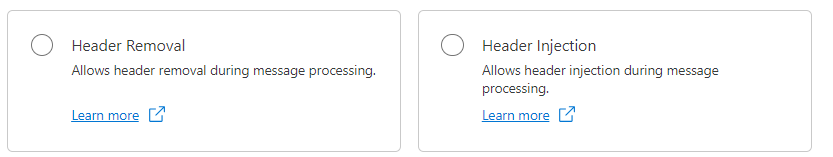
- Header Injection Policy: This policy allows you to add custom HTTP headers to either the request or the response of an API message. These headers can contain additional metadata or information that needs to be included for communication between the client and server. The policy takes effect before sending the request or response, ensuring that the added headers are included in the message being transmitted.
- Header Removal Policy: Conversely, the Header Removal policy removes specified HTTP headers from either the request or the response of an API message. This can be useful for security reasons, compliance with certain standards, or optimizing the message size by removing unnecessary headers. Similar to the Header Injection policy, the Header Removal policy also takes effect before sending the request or response, ensuring that the specified headers are excluded from the message being transmitted.
4. Quality of Service (QoS) Policies:
QoS policies focus on ensuring the performance and reliability of APIs. They may include policies for enforcing Service Level Agreements (SLAs), controlling traffic spikes through rate limiting or spike control mechanisms, and implementing caching to improve response times and reduce server load. QoS policies help optimize API performance and ensure a consistent experience for API consumers.
- HTTP Caching: The HTTP Caching policy allows you to cache HTTP responses returned by your API. Caching involves storing copies of frequently accessed resources temporarily, so subsequent requests for the same resource can be served from the cache rather than from the origin server. This helps in reducing the response time for user requests and also reduces the load on the backend server. By caching responses, you can improve the overall performance and scalability of your API.
- Rate Limiting: Rate Limiting is a traffic management policy that controls the rate of incoming requests to an API. It allows you to define the maximum number of requests that can be processed within a specified period of time, often referred to as the “rate limit window”. Once the rate limit is reached, the API will start rejecting requests or returning error responses (such as HTTP 429 Too Many Requests). Rate limiting helps prevent API abuse, ensures fair usage of resources, and protects against denial-of-service (DoS) attacks by limiting the number of requests a client can make within a given time frame.
- Spike Control: Spike Control is a policy that complements rate limiting by ensuring that sudden spikes in traffic do not overwhelm the API. It allows you to define thresholds for the number of messages processed within a specified time period. If the incoming message rate exceeds this threshold, the policy can queue the excess requests for processing later, or it can apply other strategies to handle the spike in a controlled manner. Spike control helps maintain the stability and availability of the API during periods of high demand, preventing performance degradation or downtime due to unexpected traffic spikes.
5. Troubleshooting Policies:
Troubleshooting policies are used for debugging and monitoring purposes. They enable the logging of incoming requests and responses, allowing administrators to track API usage, identify errors, and diagnose issues. Troubleshooting policies are essential for maintaining the health and reliability of APIs and diagnosing problems quickly when they arise.
- Message Logging: The Message Logging policy allows for the logging of custom messages utilizing data from incoming requests, responses from the backend, or details from other policies applied to the same API endpoint. This feature is valuable for troubleshooting, monitoring, and auditing API interactions, providing insights into the behavior and performance of the API