Are you worried about data breaches and cyber threats? This blog post discusses how to use secure properties in Mule 4 effectively to protect sensitive information within your Anypoint Platform applications.
Let’s start by discussing why secure properties are important. By using encryption, you can protect your confidential information from prying eyes. Plus, you can easily manage all your credentials from one convenient place, making it a breeze to stay organized. Most importantly, taking these steps helps prevent data breaches and keeps unauthorized access at bay. Let’s work together to ensure your information remains secure!
Here’s a Step-by-Step Guide (with 2 options discussed) for creating Secure Properties in Mule 4;
Method 1: Encrypting Individual Properties
- Identify Sensitive Data: Determine the specific properties that require encryption.
- Encrypt Values: Use a secure encryption method to encrypt the sensitive values.
- Format Properties File: Enclose the encrypted values within ![value] in your properties file.
Method 2: Using the Secure Properties Generator
- Access the Generator: Locate the Secure Properties Generator tool in Anypoint Studio.
- Configure Settings: Specify the desired encryption algorithm and keystore.
- Generate Encrypted Properties: Use the generator to create a secure properties file with encrypted values.
Here’s how to secure your configuration properties;
- Choose Your File Format
- Mule 4 lets you use either YAML (.yaml) or Spring-formatted Properties (.properties) files to store your sensitive information.
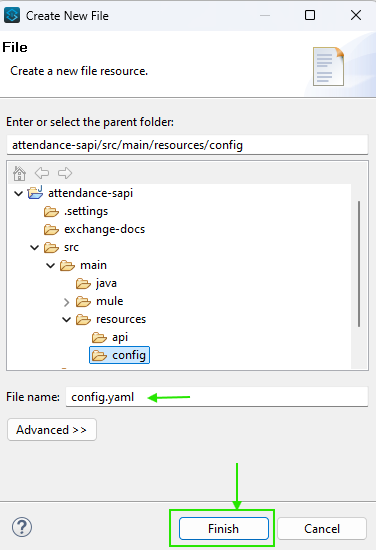
Create the File
- Navigate to your project’s src/main/resources directory and right-click to create a new file. Choose either .yaml or .properties as the extension based on your preference.
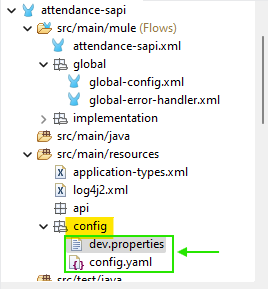
This approach offers flexibility by accommodating both popular file formats. Placing the file in src/main/resources ensures proper project organization.
The config.yaml file needs to be secured to protect sensitive information.
Method 1: Using the Secure Properties Tool
To protect your configuration data, use the Secure Properties Tool to encrypt it.
- Download the Secure Properties Tool JAR.
- Organize your configuration file and the JAR in the same directory.
Step 1:
To secure your text string, follow these steps;
- Open your terminal and navigate to the directory containing the secure-properties-tool.jar.
- Run the encryption command to protect your sensitive information.
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool \
<method> \
<operation> \
<algorithm> \
<mode> \
<key> \
<value> \
–use-random-iv [optional]
For Example :
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool \
string \
encrypt \
Blowfish \
CBC \
mule \
“test_trainee”
The tool returns:
eTQGQtOrzi+oM3Y+ELEh0Q==
Step 2:
Beyond individual strings, you can encrypt complete configuration files like YAML or Properties.
Preparation:
Configure Your File: Ensure you have a YAML or Properties file containing the sensitive information you want to protect. Here’s an example:
username: “test_trainee”
password: “123456”
Encryption Process:
Run the Command: Execute the following command syntax to encrypt all values within the file:
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool \
<method> \
<operation> \
<algorithm> \
<mode> \
<key> \
<input file> \
<output file> \
–use-random-iv [optional]
Example:
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool \
file \
encrypt \
Blowfish \
CBC \
mule \
config.yaml \
encrypt.yaml
Verifying the Results:
After running the command, the tool generates an encrypted output file (encrypt.yaml) where the values are now unreadable:
username: “![eAuZs4QmJKDqnOy25/XGCXQmYlQDMm2G]”
password: “![ZYTHOlLyXj3AnCJDJlf6Pg==]”
Method 2: Using the Secure Properties Generator
To incorporate the Secure Configuration Properties module into your Mule 4 application, follow these steps:
- Download from Anypoint Exchange:
- Access Anypoint Exchange and download the module.
- Add the downloaded module to your Mule 4 project.
- Add as a Maven Dependency:
- Include the following dependency in your pom.xml file:
XML
<dependency>
<groupId>com.mulesoft.modules</groupId>
<artifactId>mule-secure-configuration-property-module</artifactId>
<version>1.2.7</version>
<classifier>mule-plugin</classifier>
</dependency>
Implementing Secure Properties in Mule
1) Configuration File: Create a file to store encrypted sensitive data.
2) Encryption Key: This key is used to encrypt and decrypt your sensitive data. Pass it as a runtime argument: -Dtoken=mule.
3) Encryption Configuration: Ensure you provide the specific encryption algorithm and mode used to protect your data.
4)Accessing Secure Properties: Once you’ve configured your secure properties, you can access them within your Mule project for various purposes. Here’s how:
– Global Configuration:
- Syntax: Use the ${secure::property.name} format to reference secure properties in any global configuration file.
- Example: If your property name is api_key, you would use ${secure::api_key} to access its encrypted value.
– DataWeave:
- Function: Utilize the p(‘secure::property.name’) function within DataWeave expressions to integrate secure properties.
- Example: Imagine you have a DataWeave expression that requires the username from your encrypted properties. You can access it using p(‘secure::username’).
5) Automatic Decryption: Mule Runtime handles decryption, just provide the key as a VM argument.
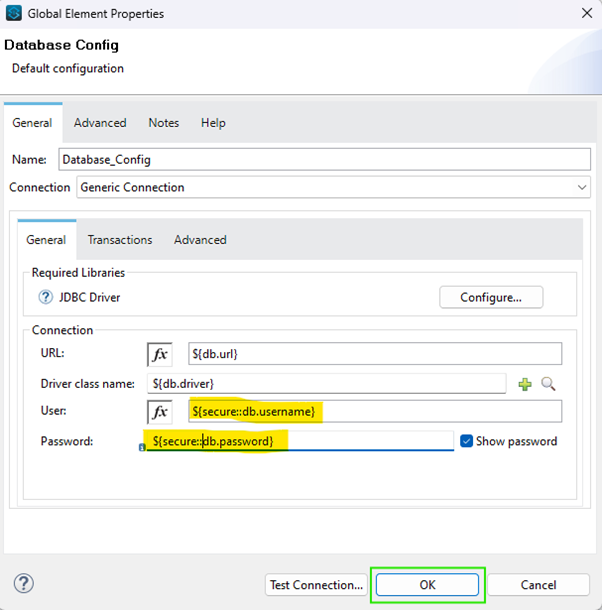
Implement these strategies to enhance the security of your Mule 4 applications. Encrypting sensitive data, such as API keys and passwords, aligns with security best practices and protects your application from potential vulnerabilities.