Introduction:
In today’s digital era, data security is paramount. With the increase in data breaches and cyber threats, ensuring that sensitive information within applications remains secure is crucial. MuleSoft’s Anypoint Platform offers various tools to enhance data security, one of which is the use of secure properties in Mule 4. This blog post will guide you through the concept of secure properties, their importance, and how to configure them in Anypoint Studio effectively.
Why are Secure Properties Important?
- Data Protection:
Secure properties protect sensitive data by encrypting it, ensuring that even if unauthorized access to the configuration files occurs, the data remains unreadable. - Centralized Management:
Secure properties allow for centralized management of sensitive information, making it easier to update and manage credentials across multiple environments without hardcoding them into applications. - Risk Mitigation:
By encrypting sensitive data, the risk of exposure through logs, configuration files, or unauthorized access is significantly reduced.
Steps to Creating Secure Properties in Mule 4
In this blog, we will configure secure properties using two methods:
- First Method:
We can encrypt the whole file or encrypt individual property. For individual property, we can define secure properties in the file by enclosing the encrypted values between the sequence![value]. - Second Method:
For an alternative approach using the Secure Properties Generator.
Create a Configuration Properties File:
To secure your configuration properties, start by creating a YAML (.yaml) or Spring-formatted Properties (.properties) file in your Mule project. This file will hold the properties you want to secure, and you can place it in the src/main/resources directory of your project. The Mule Secure Configuration Properties extension module allows you to work with both YAML and Properties files.
Here’s how to do it:
1.Open Anypoint Studio.
2. Navigate to Your Project Folder: Go to src/main/resources.
3. Create a New File: Right-click, select New -> File, and choose either .yaml or .properties as the file extension.
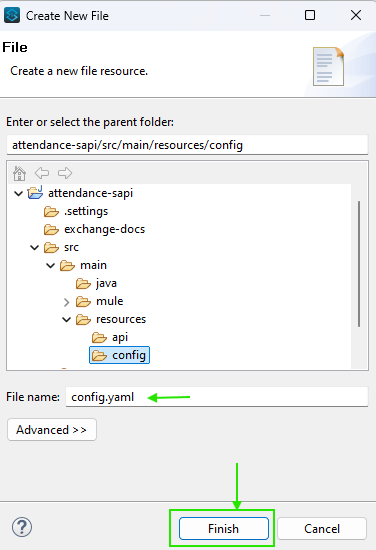
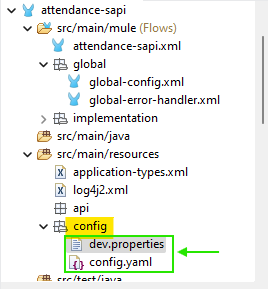
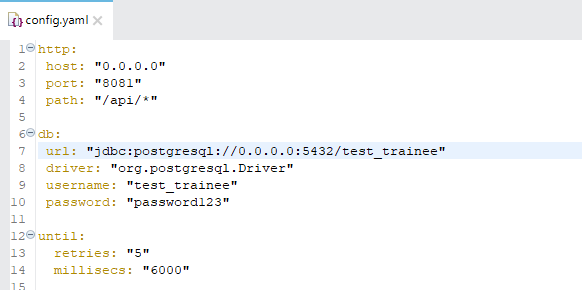
The following config.yaml file contain non-encrypted configuration properties values:
config.yaml (sample yaml file)
First Method: Encrypting Properties Using the Secure Properties Tool (JAR)
To secure your configuration properties in Mule 4, you can use the MuleSoft Secure Properties Tool (JAR). Below are the detailed steps to encrypt properties either as individual strings or within a .yaml or .properties file.
Download and Set Up the Secure Properties Tool:
Download the Secure Properties Tool JAR:
- Visit the MuleSoft documentation page and Download link: Secure Properties Tool Jar file.
Place Files in the Same Location:
- Move the ‘
secure-properties-tool.jar‘ and your unencrypted YAML or Properties file to the same directory on your local machine.
Step 1: Encrypt a Text String:
You can encrypt a simple text string by running the following command in your terminal:
- Open Command Prompt or Terminal: Navigate to the directory where the ‘
secure-properties-tool.jar‘ is located. - Run the Encryption Command: Use the following syntax to encrypt the string:
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool \
<method> \
<operation> \
<algorithm> \
<mode> \
<key> \
<value> \
--use-random-iv [optional]Example :
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool \
string \
encrypt \
Blowfish \
CBC \
mule \
"test_trainee"
- The tool returns:
eTQGQtOrzi+oM3Y+ELEh0Q==
Example of encryption: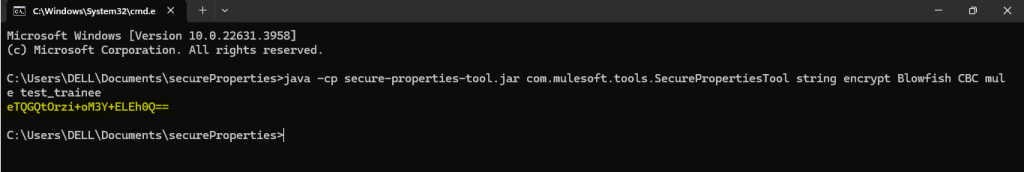
Step 2: Encrypt Properties Inside a File:
In addition to encrypting strings, you can also encrypt entire files, such as .yaml or .properties files.
Prepare Your File:
- Ensure you have a
.yamlor.propertiesfile with the content you want to encrypt. For example:
username: "test_trainee"
password: "123456"Run the File Encryption Command:
- Use the following syntax to encrypt all values inside the file:
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool \
<method> \
<operation> \
<algorithm> \
<mode> \
<key> \
<input file> \
<output file> \
--use-random-iv [optional]Example:
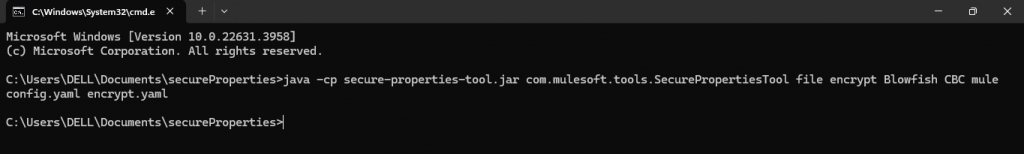
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool \
file \
encrypt \
Blowfish \
CBC \
mule \
config.yaml \
encrypt.yaml
- Replace
config.yamlwith your input file name andencrypt.yamlwith the desired output file name.
Review the Encrypted File:
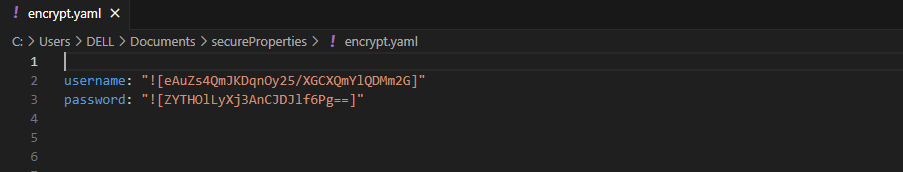
- After running the command, the tool generates an encrypted output file (
encrypt.yaml) with the content encrypted, for example:
username: "![eAuZs4QmJKDqnOy25/XGCXQmYlQDMm2G]"
password: "![ZYTHOlLyXj3AnCJDJlf6Pg==]"
Example of encryption:
Second Method: Encrypting Properties Using the Secure Properties Generator
For an alternative approach to securing properties, you can use the Secure Properties Generator. To follow a detailed, step-by-step guide on this method, refer to the instructions provided in this https://www.dwinsoft.in/blog-details/encryption-and-decryption-in-mule. This guide will walk you through the process of encrypting and decrypting properties in Mule using the Secure Properties Generator tool.
Configure Secure Property Module and Dependency in The Project
Include the Secure Configuration Properties module in your project and set it up accordingly. You can download this module directly from Anypoint Exchange. Alternatively, you can add it as a Maven dependency:
<dependency>
<groupId>com.mulesoft.modules</groupId>
<artifactId>mule-secure-configuration-property-module</artifactId>
<version>1.2.7</version>
<classifier>mule-plugin</classifier>
</dependency>
Using Secure Properties in Your Mule Project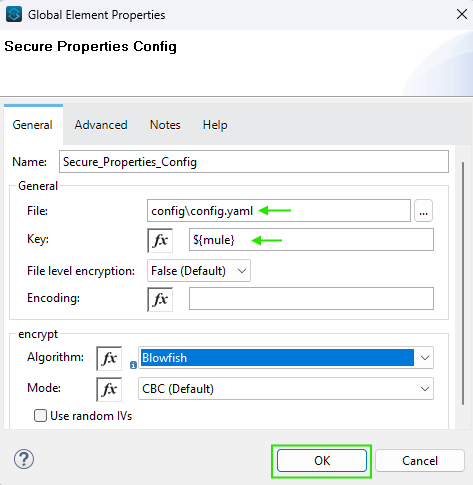
- File: Name your properties file where the secure properties are stored.
- Key: This is the encryption/decryption key. You will pass this key as a program argument during runtime, like this:
-Dtoken=mule. - Algorithm and Mode: Ensure you specify the correct encryption algorithm and mode that you used to encrypt the properties.
- Using Secure Properties in Your Project:
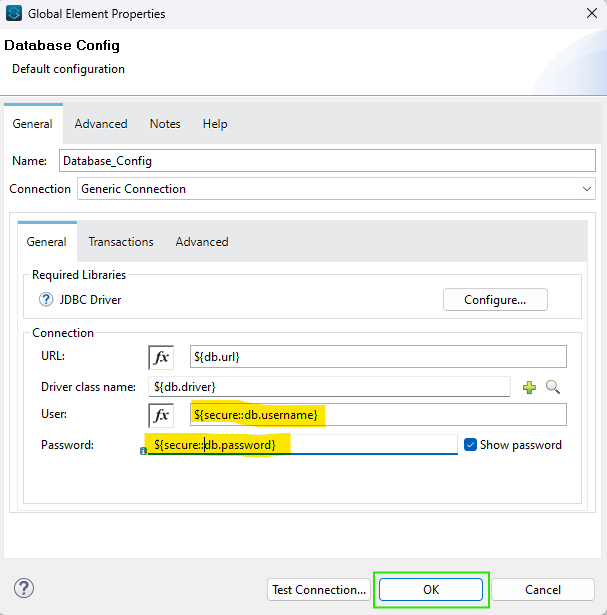
- In any global configuration, you can reference a secure property like this:
${secure::property.name}. - In DataWeave, you can use the secure property like this:
p('secure::property.name').
For example, if you have encrypted properties for
usernameandpassword, you can use them in your project as:javaCopy codeencrypted_username_value: p('secure::username') password_value: p('secure::password') - In any global configuration, you can reference a secure property like this:
- Automatic Decryption: Mule Runtime automatically handles the decryption process. All you need to do is pass the decryption key as a VM argument during runtime, and you’re good to go!
Run your application and Ensure that the properties are correctly encrypted and used in your flows.
Conclusion:
By following these steps, you can effectively secure sensitive configuration properties in your Mule 4 applications. Encrypting these properties ensures that your sensitive data, such as API keys and passwords, remain protected and compliant with security standards. Whether using a Properties file or opting for YAML with external encryption, Mule 4 provides flexible and robust ways to secure your application configurations.
This blog will guide you through securing your configuration files in Mule 4, ensuring your sensitive data remains protected and compliant with best practices.